DDoS Protection
What is DDoS Protection?
DDoS protection refers to the tools and strategies used to detect and defend against Distributed Denial-of-Service (DDoS) attacks that are cyber assaults that aim to overwhelm a target’s networks or services with malicious traffic. In a DDoS attack, a perpetrator effectively floods a website, server, or network resource with so much fake traffic that legitimate users cannot access it, much like an unexpected traffic jam clogging the highway and blocking real travelers. Such attacks can be highly disruptive, causing downtime, revenue loss, and damage to an organization’s reputation if not properly mitigated.
DDoS protection involves rapidly detecting the onset of an attack, differentiating malicious traffic from normal user traffic, and filtering or absorbing the bad traffic before it can impact the target. The goal is straightforward: keep websites, applications, and networks reachable and responsive no matter how much junk traffic attackers throw at them.
It’s worth noting that modern DDoS protection is multi-layered. Attacks can bombard different layers of the network (volumetric floods at the network layer, protocol exploits, or targeted application-layer attacks), so effective protection involves multiple techniques working in tandem. For instance, network-level defenses might handle high-volume floods while application-layer firewalls inspect more subtle malicious requests. The best DDoS protection strategies utilize a mix of on-premises appliances, cloud-based scrubbing centers, and distributed edge sensors, all coordinated to stop attacks quickly and avoid any single point of failure.
Why is DDoS Attack Protection Crucial?
A successful DDoS attack can have devastating consequences for businesses. At the most basic level, it causes service downtime. Websites go offline, APIs and applications become unreachable, and users are unable to transact or get information. This downtime directly translates to lost revenue and productivity for any online business or communication service provider. Studies and industry reports have repeatedly shown that even an hour of outage can cost large enterprises thousands or millions in lost sales and operational delays.
Beyond the immediate financial hit, there’s a reputational cost. Customers and partners lose trust when a service is frequently down or sluggish due to attacks. In today’s hyper-competitive environment, users expect reliability; if a company’s digital services are perceived as unstable or easily disrupted, customers may take their business elsewhere. News of a successful DDoS attack or prolonged outage can quickly spread and damage a company’s brand image. In sectors like finance or healthcare, such incidents can be especially harmful as clients need absolute assurance of service availability and security.
How is DDoS Protection Applied?
DDoS protection works by continuously monitoring network traffic, detecting threats in real time, and blocking malicious data before it overwhelms systems. It operates as an always-on security layer designed to distinguish harmful spikes from legitimate user activity. Below are the key ways DDoS protection is applied to identify, mitigate, and adapt to evolving threats:
- Monitoring & Baselines: The system learns normal traffic behavior to quickly detect suspicious surges or anomalies that may signal an attack.
- Threat Detection: Intelligent analytics and deep packet inspection identify known and emerging DDoS patterns, including SYN (synchronization) floods, botnet activity, and multi-source traffic anomalies. AI- and ML-driven tools, such as User and Entity Behavior Analytics (UEBA), enhance early detection by identifying deviations from normal network behavior.
- Real-Time Mitigation: Once a threat is detected, the system activates countermeasures such as rate limiting, intelligent traffic filtering, and, when necessary, routing through scrubbing centers to remove malicious packets. These methods effectively reduce attack impact and maintain service availability, though they can introduce minor latency or brief routing delays while filtering legitimate traffic.
- Adaptive Defense: As attacks evolve (e.g., from network floods to application-layer attacks), the protection system adjusts dynamically to block new vectors and ensure consistent availability.
DDoS Protection Best Practices
Following these best practices strengthens your organization’s resilience and ensures you’re ready to respond to modern DDoS threats quickly and effectively. Here are essential DDoS practices:
- Establish Traffic Baselines: Know what normal traffic looks like so you can spot anomalies quickly.
- Prioritize Critical Assets: Identify and safeguard your most essential systems like, web servers, APIs, and infrastructure components.
- Harden Your Network: Keep systems patched, enforce strong passwords, use multi-factor authentication (MFA), and educate staff to prevent accidental compromise.
- Build Resilience: Provision extra bandwidth, use CDNs or anycast to distribute traffic, and ensure systems can scale during sudden spikes.
- Create a Response Plan: Define roles, mitigation timelines, and escalation protocols. Test the plan regularly.
- Use Layered Defenses: Combine on-premise or edge-based protection (like RADInsight TI) with cloud-based mitigation to cover all attack vectors.
Limitations of Traditional DDoS Mitigation Approaches
Conventional DDoS protection solutions often rely on centralized, cloud or data center-based mitigation, which can leave security gaps that attackers exploit. Typically, when a large attack is detected, victim organizations or their Internet Service Providers will reroute incoming traffic to scrubbing centers, centralized cleansing points that filter out malicious packets before forwarding legitimate traffic onward. While this method can handle high-volume floods, it has notable drawbacks. For one, it adds latency and complexity, since all traffic (malicious or not) must travel through a distant mitigation center. Furthermore, short-lived or low-volume attacks may not even trigger the thresholds required to initiate scrubbing, meaning smaller-scale DDoS bursts can slip through unnoticed.
Traditional solutions that focus solely on massive volumetric attacks might miss these “slow and low” assaults, as well as insider-originated attacks, leaving networks vulnerable.
It is important to note that scrubbing centers operate primarily at Layer 3 (L3), filtering routed IP traffic. However, if a cloud service provider or enterprise uses Layer 2 (L2) connectivity, such as direct, non-routed links, those connections bypass scrubbing infrastructure entirely. This creates an exposure gap where attacks can still reach critical systems without inspection.
Another challenge is visibility and responsiveness. If organizations rely on generic cloud-based DDoS protection services, they might have limited insight or control. Inconsistencies in cloud provider security responsibilities can lead to unprotected gaps, and not all providers guarantee rapid mitigation or detailed reporting in the event of an attack. Centralized mitigation also creates potential single points of failure, an overloaded scrubbing center or a failure in the redirection mechanism could itself become a bottleneck. These limitations in traditional approaches underscore the need for a more distributed and proactive defense strategy.
DDoS Protection: RAD’s Approach
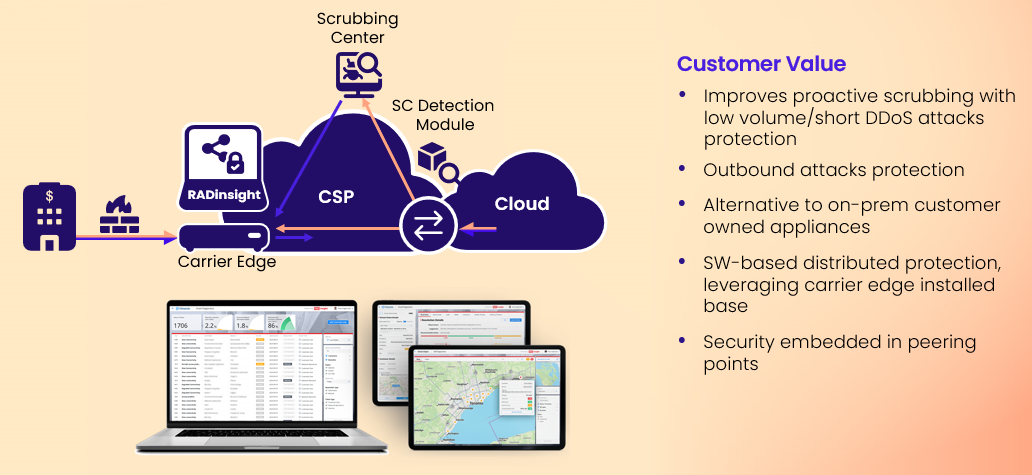
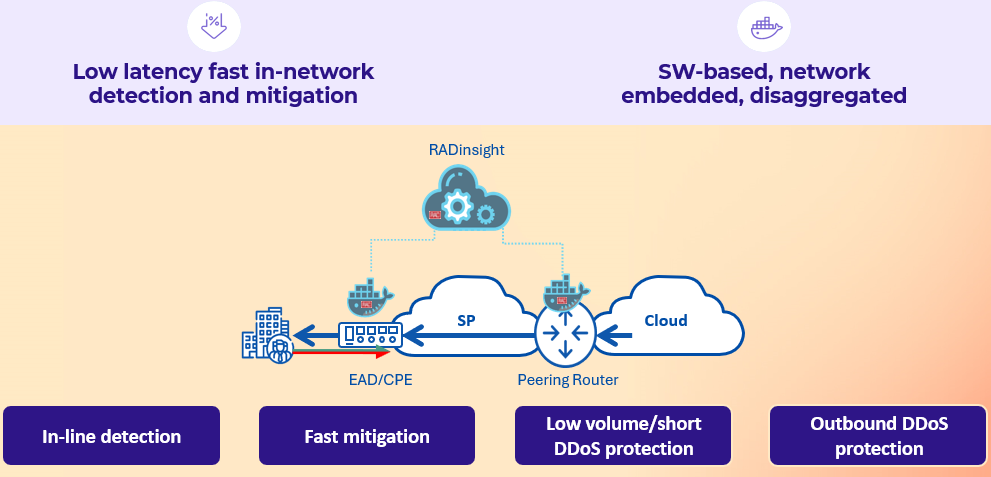
RAD addresses these challenges by embedding DDoS protection at the network edge, closer to where attacks actually originate or where their impact is first felt. Instead of hauling all traffic to a central location, RAD’s solution distributes the detection and mitigation intelligence out to the edge of the network, such as customer premises equipment, provider edge routers, L2 interconnects, and peering points. By moving the first line of defense to the edge, malicious traffic can be identified and filtered in real time, within seconds, right where it enters (or leaves) the network.
RAD’s RADinsight TI DDoS Protection software-based solution runs on the hardware already deployed at these edges, making it a cost-effective, high-performance, network-embedded security layer. This distributed approach brings several advantages. DDoS attack detection is powered by AI and machine learning, which analyze traffic patterns at the edge to swiftly distinguish legitimate usage from suspicious spikes or behaviors. Thanks to this intelligence, the system can catch both known attack signatures and zero-day anomalies (including complex, orchestrated multi-vector attacks) before they escalate. Crucially, mitigation occurs locally: when a DDoS threat is identified at a given edge device, that device (or its nearest neighbor) can automatically block or rate-limit the malicious traffic at the source, using techniques like access control lists, without needing to reroute it through a distant scrubbing center.
This edge-centric DDoS protection means there is no need for extensive traffic rerouting that could introduce latency or create additional failure points. Legitimate users connected through that edge experience minimal disruption, as bad traffic is neutralized close to its origin. Additionally, network-wide scalability is inherently built in: as a service provider or enterprise network grows and adds more edge devices or customer sites, the DDoS protection expands naturally with it. The security coverage scales with network growth and decentralization, since each new edge node can become another enforcement point in the distributed defense mesh. By leveraging existing network equipment, RAD’s solution avoids costly infrastructure overhauls and can be offered by Communications Service Providers as a managed DDoS protection service to their business customers for added value.
Another important benefit of RAD’s edge approach is the ability to stop both inbound and outbound DDoS traffic. Traditional thinking often focuses on inbound attacks (external attackers trying to take down your services), but what if a device inside your network is compromised and starts participating in a botnet attack against others? RAD’s DDoS protection at the edge monitors traffic in both directions, so it can detect and mitigate outbound attack traffic from infected or hijacked devices within your network, preventing your infrastructure from unwittingly contributing to DDoS campaigns. This two-way protection safeguards service providers’ networks and their reputation, ensuring they aren’t the source of attacks, while also protecting their end customers from incoming floods.
Key Benefits & Features of RAD’s Edge DDoS Protection:
- Comprehensive Threat Coverage: AI-driven threat intelligence identifies both well-known DDoS attack patterns and novel, zero-day exploits. The system can recognize multi-vector “orchestration” attacks that blend different techniques, providing broad protection against volumetric floods, protocol attacks, and application-layer (Layer 7) assaults.
- Rapid Edge Mitigation: Attack detection and blocking occur within seconds at the edge, dramatically reducing response time. The solution acts as a distributed firewall at each edge point, so that malicious traffic is filtered out immediately where it’s detected, serving as an instant first line of defense and keeping critical services available. Even short-lived burst attacks can be thwarted before they do damage.
- No Traffic Rerouting Needed: Unlike traditional DDoS mitigation that may divert traffic to centralized scrubbing centers, RAD’s approach requires no rerouting of traffic off its normal path. Legitimate user traffic continues through the usual low-latency route, while harmful packets are dropped at the edge. This means no added network latency or bottlenecks and no new single point of failure introduced for mitigation, preserving the user experience even during an attack.
- Network-Embedded and Scalable: The DDoS protection software runs on existing edge devices (such as RAD’s Ethernet access devices or universal CPEs) already in the network, leveraging their processing capabilities. This disaggregated, pure software-based deployment is highly scalable: as you extend your network or add customers, each additional device increases the overall defensive grid. The architecture avoids dedicated hardware appliances, making it a cost-effective solution that scales naturally with your business growth.
- Inbound and Outbound Attack Prevention: RAD’s network edge solution protects both inbound and outbound traffic, a unique advantage. It shields your infrastructure and services from incoming DDoS floods, and at the same time prevents any compromised internal devices or customer networks from launching outbound attacks through your network. This two-way protection enhances overall security and trust, ensuring compliance and stability across the board.
RADinsight TI – Turning the Edge into a Shield Against DDoS
RAD’s RADinsight TI DDoS Edge Protection solution encapsulates all these benefits into a single platform. It is delivered as a SaaS (Software-as-a-Service) offering combined with on-premise edge enforcement, closing the security gaps left by legacy approaches. By using network-embedded threat intelligence at the edge, RADinsight TI empowers communications service providers to offer managed DDoS protection services to their customers without overhauling their network architecture. In essence, it brings cloud-grade DDoS mitigation capabilities right to the network edge, where they can react faster and more precisely. This innovative approach allows for DDoS attack detection and mitigation within seconds of an assault starting, significantly limiting the damage and ensuring that critical connectivity is maintained. Just as a healthy immune system neutralizes threats before you even notice them, RAD’s edge-based DDoS protection stops attacks in real time, keeping your network and services running smoothly.
By deploying RADinsight TI across the network edge, service providers and enterprises achieve a multi-layered defense: local protection at each site or customer premises works in tandem with any existing cloud or core-network DDoS defenses. The result is a more resilient, distributed security posture that can absorb and mitigate attacks at all levels. With DDoS attacks only growing in scale and sophistication, edge DDoS protection offers a timely solution to stay one step ahead of attackers and ensure uninterrupted service for users even under duress.
Strengthen Your Network Against DDoS Threats
In conclusion, DDoS Protection is a multi-faceted effort, combining vigilant technology, sound practices, and innovative strategies. By staying informed about the latest best practices and partnering with solution providers like RAD, businesses can stay one step ahead of attackers. Don’t wait for an attack to happen to test your defenses. Strengthen your network now with advanced DDoS protection measures.
Learn more about RAD’s DDoS Protection at the Edge by visiting our product page or reading our detailed use case on how RADInsight TI secures networks at the edge.