SaaS solution closes current security gaps
RADinsightTM TI is a software-based DDoS protection solution. Distributed over customer and network edges, it utilizes the hardware already in your network. RADinsight TI is a cost-effective, high-performance, network-embedded security solution that enables communications service providers to expand their offering with managed DDoS protection services.
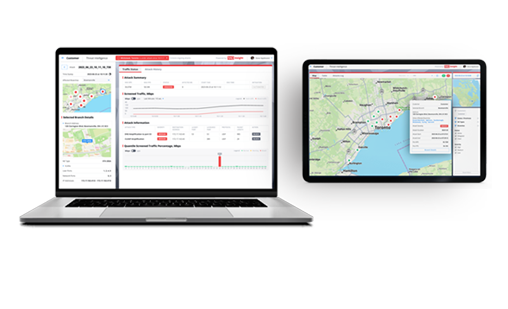
Product Highlights
Zero-day & known attacks. Orchestration attacks
Within seconds through ACL in edge devices, close to attack origin
No traffic rerouting. No additional weak point. No impact on user experience
RADinsight-TI Use Cases
 DDoS Protection at the Edge
DDoS Protection at the Edge
Related Resources
RADinsightTM-TI DDoS Edge Protection


