
Your Network's Edge®
Blog Post
You are here
Threat Intelligence at the Edge
Threat Intelligence at the Edge
Distributed Denial-of-Service (DDoS) attacks have increased dramatically, especially in terms of frequency, magnitude, and sophistication. Bot attacks are a prominent threat at the forefront of the assault toolkit. These attacks are causing significant disruptions for communications service providers (CSPs) and enterprises.
The most popular method to thwart DDoS attacks is by "scrubbing” suspicious traffic, meaning rerouting suspicious traffic to dedicated scrubbing centers where it’s analyzed. Legitimate traffic is then routed to its destination, while confirmed malicious traffic is blocked.
The Problem With Scrubbing Centers
Scrubbing centers can operate as cloud-based SaaS. They are often distributed across different geographic locations and boast virtually limitless capacity. However, out-of-band scrubbing centers add latency due to traffic rerouting. They can also be costly, especially for volumetric attacks.
Scrubbing requires manual analysis and human intervention, which adds even more latency and cost to the remediation process. Mitigating an attack that disrupts an enterprise’s normal business operation and threatens the available bandwidth and throughput of a CSP which can take up CSPs valuable time. As attacks are becoming more sophisticated, current solutions are proving to be lagging in providing adequate protection. For example, by design, cloud-based scrubbing centers focus on handling inbound traffic. However, scrubbing centers do not offer effective protection against malicious outbound traffic. This type of traffic originates from within enterprise networks and targets their assets, including data centers, servers, or firewalls.
This type of traffic is typically generated by malicious bots installed offline on enterprise hosts, or on IoT network devices to generate orchestrated attacks on enterprise assets or CSP resources. Scrubbing centers cannot detect standard enterprise services and applications. Therefore, during an outbound attack, they can’t detect abnormal traffic or infected hosts.
Additionally, enterprises may be using partnering (peering) networks to extend services beyond their main coverage area. Hence, scrubbing centers cannot address malicious traffic originating from these sources. This situation leaves enterprise assets susceptible to potential attacks.
Other available solutions, such as enterprise firewalls, have been proven to be ineffective against volumetric attacks due to their distributed nature. In the case of inline appliances, they are also very expensive. This clearly indicates the need for a new type of affordable DDoS protection solutions. These solutions should be able to face both inbound and outbound threats. In addition, they should detect and mitigate malicious traffic as close to the attack origin as possible – and do it in seconds.
Introducing RADinsight Threat Intelligence (TI)
This is exactly what we had in mind when developing the RADinsight Edge Threat Intelligence (TI) solution for edge protection of CSP networks and enterprise assets.
RADinsight TI serves as a first line of defense by detecting and mitigating incoming volumetric attacks, stepping in before the scrubbing center is activated, or when the attack volume falls below the threshold established in the scrubbing center. RADinsight TI provides network-embedded security to detect and mitigate outbound DDoS attacks.
Another difference that sets RADinsight TI apart from current solutions, is that it operates as close to the source of attack as possible. This means the L2 demarcation points between the enterprise and service provider networks, and between carrier networks (inter-carrier demarcation), thus protecting the CSP network from resource depletion.
RADinsight TI employs advanced traffic sampling and anomaly detection ML algorithm that protects against volumetric known and zero-day attacks within seconds. It also has the ability to identify the attack’s origin.
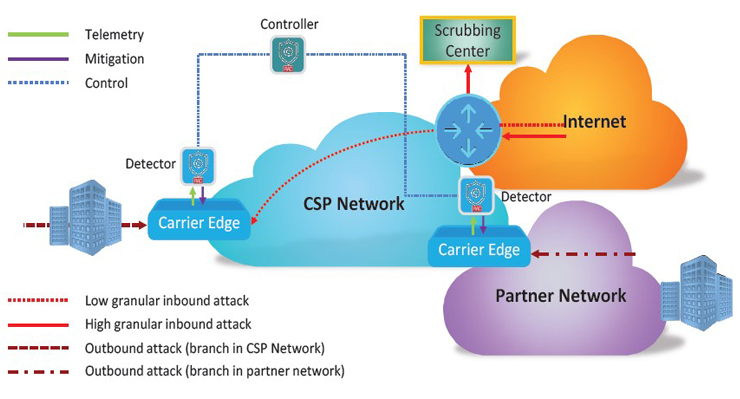
The SaaS platform operates on traffic running through carrier and network edge devices installed on the network. RADinsight TI does not create additional weak points, compromise device bandwidth, or add latency in the network, as it is not an inline solution.
Beyond technology innovation, we designed RADinsight TI with the purpose of enabling CSP to offer higher value to their business customers by relying on their own underlay network, rather than on over-the-top (OTT) solutions.

